PETRA CIPHER
Petra Cipher is a database encryption solution that protects the asset and brand value of companies and
prevents the loss of important data through encryption. It complies with security-related legislations and
compliances including the Personal Information Protection Act and the Standards for Measures to Secure Safety of Personal Data.
Petra Cipher also ensures the availability of the system by analyzing possible issues from encryption in
advance and supports highly confidential, integrity, and stable services through advanced technology such as
triple redundant key servers and prevention of double encryption.
Related Legislations & Compliance
Key Features
Safe key generation and management
- Generates safe initial keys, and encrypts and saves generated data keys
- Safely manages keys by setting expiration dates

Strict access control and log management
- Applies access control with multiple conditions such as database accounts, IPs, and system names
- Provides log management and query screen on the history of decryption and encryption

Perfect linkage with database access control (Petra)
- Provides integrated UI for consistent rule management of database user control
- Controls decryption and encryption based on the user’s IP if the user passes through database access control

Prevents query of large data decryption
- Prevents large data exposure by controlling the volume of data decryption

Full encryption and partial encryption in the unit of a column
- Encryption setting in the unit of a column
- Partial encryption with just a column of a specific position

Dual redundant key management servers and local key management
- Maintains the service through dual redundant key servers even during active server failure

Strengths
-
High-performance and high-functioning APIs
- Ensures efficient management after encryption by providing separate APIs for session settings and saving logs
-
Stable deployment support
- Supports triple redundant key management servers (dual redundant key servers + Local key management)
- Uses pre-apply mode verified at numerous clients
-
Database access control and encryption linkage
- Provides integrated UI for consistent rule management of database user control
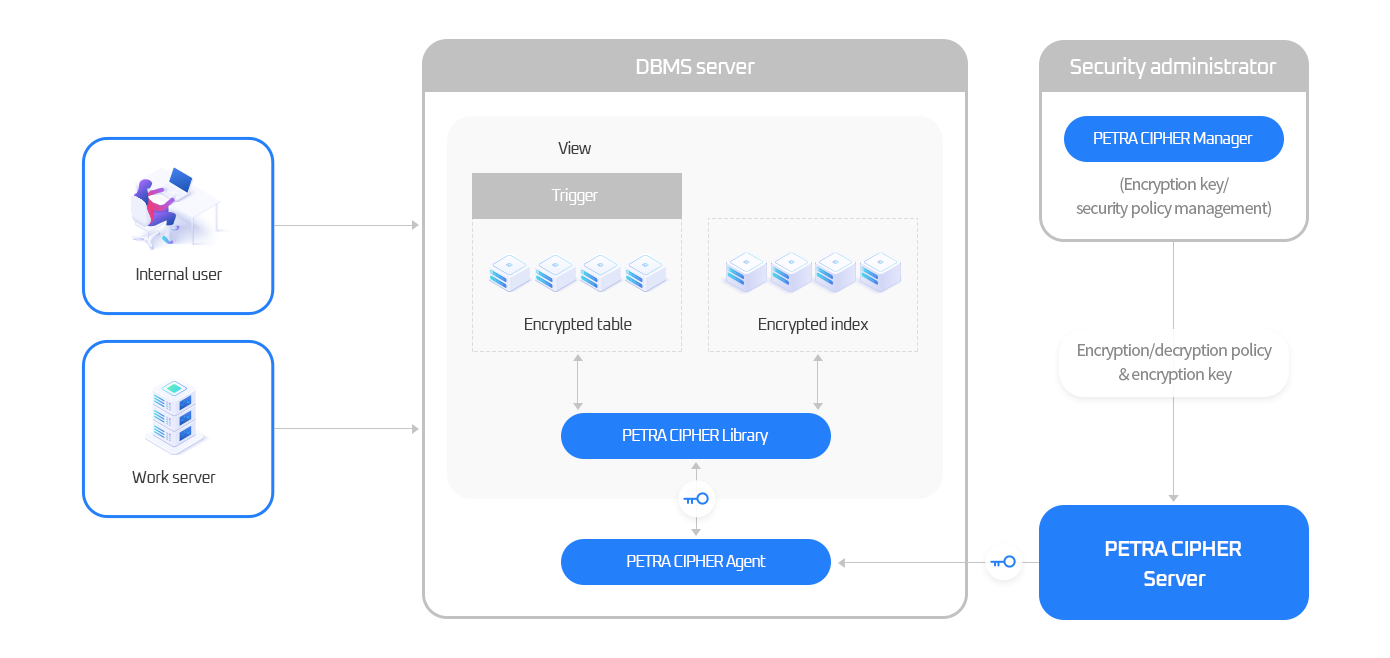
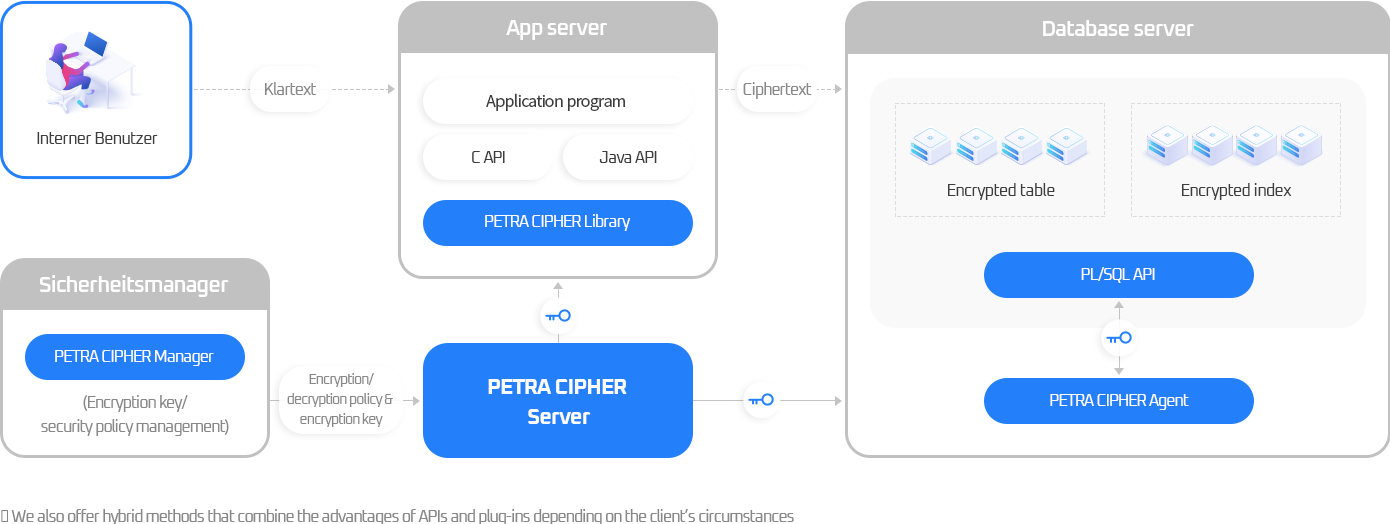
Petra Cipher Configuration Diagram
Plug-In
- Installs encryption/decryption libraries in the database server
- Encrypts without modifying the application
- Maximizes performance using C-based formulas and minimizes PL/SQL logic
API
- Installs encryption/decryption libraries in the application server
- Provides various APIs such as Java, C, JAVA, and PL/SQL to be compatible with applications and batch processing
- Provides encryption for heterogeneous DBMS independent of DBMS