PETRA
Petra is a database access control solution that ensures data security by controlling access to databases and
privileges to SQL execution. It complies with security-related legislations and compliances including the Personal
Information Protection Act, the Regulation on Supervision of Electronic Financial Transactions, the Personal
Information and Information Security Management System, and IT General Controls.
Petra provides convenient management and security by linking with external systems, including
ESM, OTP, LDAP, and multi-factor authentication, while controlling data in the unit of an object by analyzing
SQL in detail. It secures accountability in case of data leakage and exposure by recording database access and
SQL execution in real-time to prevent errors.
Related Legislations & Compliance
Key Features
Database login (access) control based
on various attributes
- Controls various access environments such as
Petra IDs, IPs, database accounts, and access software - Supports multi-factor authentication
such as OTP and SMS

Detailed access control on user behavior
- Access control by SQL type
- Access control by the unit of an object
(table or column) - Enables control in the unit of a pattern

Various audit logging of user access and behavior
- Saves session information of logins to DMBS and logs the SQL order of execution at each session
- Saves the number of data queries and bind variables

Monitoring of warning report
- Provides a warning function for security violations
- Provides various reports on logins, SQL execution,
and SQL block - Provides various functions for advanced search

Safe log management
- Saves the log into a file on the administrator’s PC
- Saves the log separately to the integrated log server
- Prevents forgery and alteration of access logs and deletion and changing security audit logs

Segmented security operation
- Ensures enhanced security
by managing authorities by administrators and
managing logins based on certifications - Provides operation log of administrators
Strengths
-
Control access policies and
central log management- Convenient centralized security policy management with the master server
- Possible to expand and add a flexible database
- Consistent distribution and management of policies for all access control products
-
Non-bypass masking
- Masking based on SQL alteration
- Protects data exposure by modifying data to internal users without authority
-
Easy backup/restoration and
management- Easy backup/restoration with a dedicated repository based on memory developed by Sinsiway
- Fast large log processing
- Provides expanded SQL to search only specific partitions
-
Examples of linkage to
external systems- Linkage between the solution’s own DBMS and data by providing REST API for linkage with the solution
- Various experiences in deployment such as personnel information, OTP,
and SMS
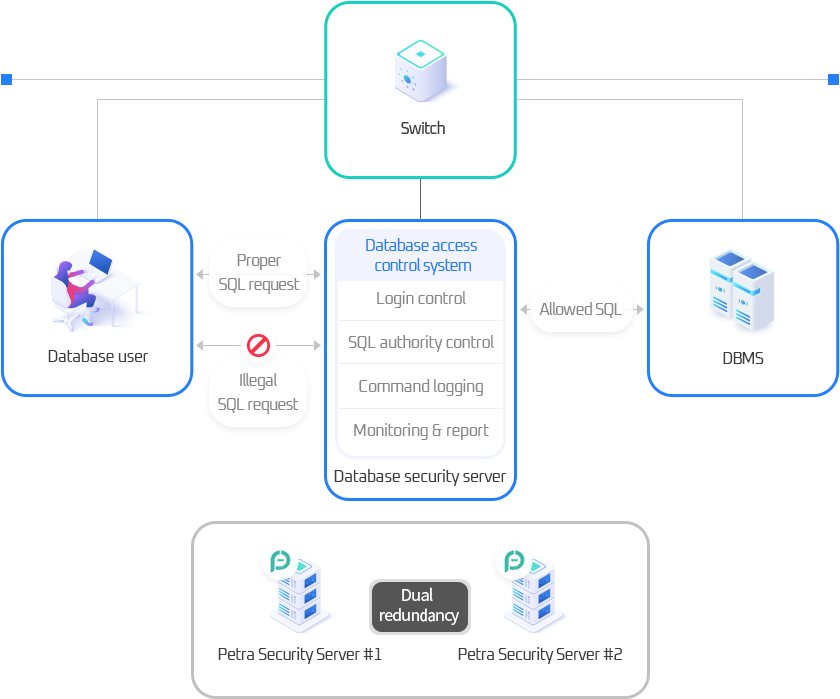
Petra Configuration Diagram
Database access logging without load on the system
- Constructs the perfect real-time security system by executing advanced database security through non-load database access logging
- Provides intuitive and convenient UI
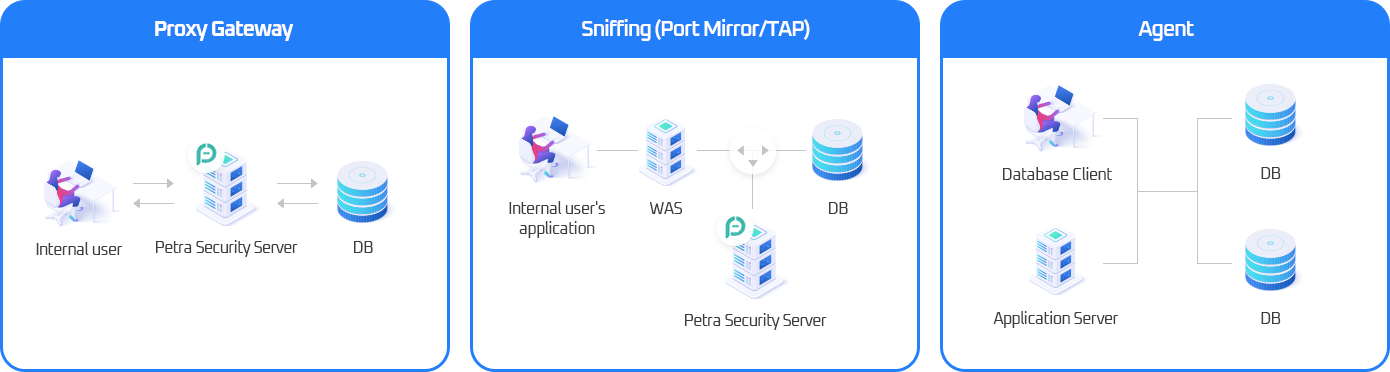
Various configurations
- Supports gateway, sniffing, agent, and hybrid methods for access control configuration of various DBMS
- Supports configuration change depending on internal work environment changes
- Provides encryption for heterogeneous DBMS independent of DBMS